Business applications play an essential role in maintaining the smooth operations, communication, and data management in a fast-changing business technology landscape. However, as cyber threats are becoming more sophisticated, the security of these applications is subject to a greater challenge. Today, 26% of all breaches involve attacks on web applications and the average number of sites visited is 94 per day. The importance of robust security measures cannot be underestimated, given that malware affects an estimated 4.1 million websites at any one time. The need for a comprehensive approach to the security of enterprise applications has never been more important, as organizations are becoming increasingly interconnected and dependent on digital platforms.
This article will explore what application security entails and why it has become critically important today. We delve into the risks of inadequate security, solutions for protection such as testing protocols, security standards and best practices, as well as the tools organizations can implement to take their application defences to the next level against modern cyber threats.
UNDERSTANDING THE IMPORTANCE OF APPLICATION SECURITY
Application security describes security measures at the application level that aims to protect software application code and data against cyber threats. It is not a single technology; rather a set of best practices, functions added to an organization’s software to help prevent and remediate threats from cyber attackers, data breaches, and other sources. Application security can occur in various stages and businesses can leverage different tools and services post-development as well. Application security potentially includes hardware, software, and procedures that could identify or minimize security vulnerabilities. You should apply application security during all.
Application security is important when your organization deals with a large amount of data. The data is an asset for attackers, and it is important to take measures to monitor and manage vulnerabilities in applications. The attackers can use it for malicious purposes, whether it is a customers’ data, proprietary product secrets, or confidential employee information. Many of today’s applications are also cloud based, which only makes them more vulnerable by transmitting data over different networks and connected to remote servers. You can minimize the risk of minor and major vulnerabilities with application security, thereby reducing your overall vulnerability profile. The better your protection, the fewer points of entry it provides for intruders. It’s much more effective to protect the applications from the very beginning, rather than waiting for potential future attacks. When it comes to mitigation, a proactive approach in application security can be advantageous.
FIVE COMPONENTS OF APPLICATION SECURITY
Authentication: To guarantee that only authorised users can access the application, software developers will build processes within it. Authentication procedures ensure that the user is who they say they are. To do this, when you log in to an application, usernames and passwords must be provided by the user. Multi-factor authentication requires more than one form of authentication.
Authorization: The user may be authorised to access and use the application after he has been authenticated. By comparing the user’s identity to a list of authorised users, the system can confirm that an applicant has permission to use this application. To match the application’s validated user credentials with an approved list of users, authentication must take place before granting permission.
Encryption: Other security measures can protect sensitive data from being seen or even used by a cybercriminal after the user has been authenticated and is using an application. In cloud applications, traffic with sensitive data travelling from the end user to the cloud can be encryption in order to ensure that information is secure.
Logging: Logs can help identify who has access to the data and how, if there is a security breach in the application. A timestamped record of which aspects of the application have been accessed and who has done so is included in the applications log files.
Application Security Testing: A necessary process to ensure that all of these security controls work properly.
KEY AREAS THAT REQUIRE SECURITY MEASURES
Web Application Security
By design, web applications operate on web servers and remain accessible through the Internet, with clients interacting via web browsers. This inherent connectivity across insecure networks opens web apps to an array of potential vulnerabilities. Moreover, many web applications now serve business-critical functions while housing sensitive customer data, rendering them high-value targets for attackers and thus cybersecurity priorities. The evolution of the Internet has resulted into some web application vulnerabilities due to which many solutions have been introduced like the web application firewall (WAF), a security tool designed to detect and block application-layer attacks.
API Security
API security is critical for modern organizations. The basis of modern microservices applications, Application Programming Interfaces allows organizations to share data and access software functionality created by others. Major data breaches due to API’s security vulnerability can expose sensitive data and result in disruption of critical business operations. Common security vulnerabilities of APIs are weak authentication, unwanted exposure of data, and failure to perform rate limiting, enabling API abuse. Specialized tools have been developed that can identify weaknesses in API’s and secure APIs in production.
Cloud Application Security
Cloud security is a complex problem, as cloud applications have a large number of moving parts and components, which tend to be transitory, often torn down and replaced by others. It is therefore difficult to gain visibility in an environment of clouds, thereby ensuring the security of all components. The developers are in charge of the establishment of declarative configurations and application code, which must be subject to security considerations. Application security in the cloud poses more challenges. As cloud environments provide shared resources, it must be ensured that users only have access to the data they are authorized to view in their cloud-based applications. In cloud applications, sensitive data is also more vulnerable due to the fact that they are transported over the Internet from a user to an application and then back again.
Mobile Application Security
Mobile devices also connect over the open internet, exposing them to threats in the absence of private networks protections. For layered protection of mobile application security, enterprises can use virtual private networks (VPNs) for employees who log in to applications remotely. IT departments should assure that employees adhere to company security policies before allowing them to use mobile devices that connect to the corporate network.
POTENTIAL RISKS ASSOCIATED WITH APPLICATION SECURITY
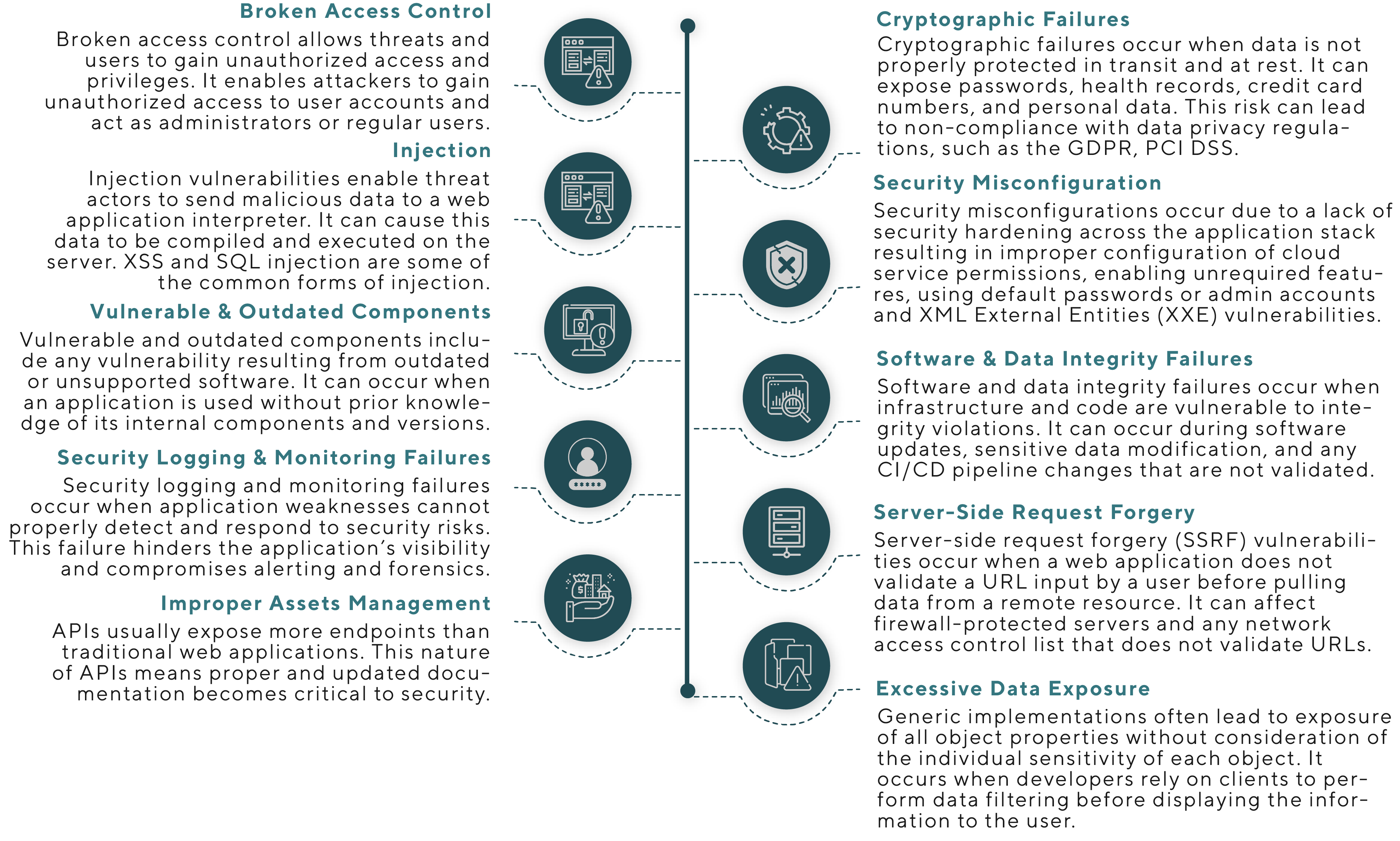
MAKING APPLICATIONS RESILIENT WITH APPLICATION SECURITY TESTING
Application Security Testing (AST) is the process of making applications more resistant to security threats by identifying and remediating security vulnerabilities. Its goal is to identify security gaps proactively which allows organizations to strengthen the application’s defences and prevent security incidents down the line when customers or employees access the applications in the real world. Application developers conduct security testing throughout the development lifecycle to resolve vulnerabilities before software release. Using compliance audits, developers verify adherence to predefined security standards across areas like access controls, encryption, and input validation. Testers attempt attacks like password cracking, system exploitation, and social engineering from both unauthenticated states and authenticated user perspectives. This multifaceted internal offensive security approach surfaces hard-to-find weaknesses that static audits may miss, especially risks arising only after login or requiring user context. Addressing the full spectrum of application vulnerabilities in staging prevents customer data, continuity and trust being impacted post-deployment.
Before properly assessing applications for security vulnerabilities, it is important to take the following considerations and parameters into account.
- Create a complete application inventory.
- Understand your applications’ business use, impact, and sensitivity.
- Determine which applications are to be tested, from publicly accessible systems such as the web and smartphones.
- Testing applications from an outsider’s perspective and performing authenticated testing to discover security issues that affect authenticated users.
- Using relevant tools that can identify vulnerabilities in source code, test applications for security weaknesses at runtime, and network vulnerability scanners.
- Testing while staging is easier to achieve relative to testing in production as it allows faster remediation of vulnerabilities.
- Disabling security systems while security tests is good as it could interfere with scanning otherwise.
- The ideal time to perform testing is during off periods to avoid any impact on the performance and reliability of production applications.
- While making a report, security teams must ensure comprehensiveness and should only record the most relevant insights from automated reports as it would be difficult for non-security experts to consume the report.
The following are the types of Application Security Testing that an organization can leverage to strengthen their application security against threats throughout the development lifecycle and post-deployment.
- Static Application Security Testing (SAST) – Evaluates application source code or compiled versions for security flaws without executing programs. Useful for finding bugs and misconfigurations early in development.
- Dynamic Application Security Testing (DAST) – Analyses applications while in a running state to detect vulnerabilities such as injection flaws or improper session management. Simulates real attacks against deployed applications.
- Interactive Application Security Testing (IAST) – Combines elements of SAST and DAST to analyse applications in an interactive state for risks that span code, runtimes, system calls and data flows. Provides automated testing signals within Software Development Life Cycles.
- Runtime Application Self-Protection (RASP) – Uses sensors placed into production applications to monitor, detect, and block threats in real-time like SQL injections or unauthorized API calls as attacks occur. Secures apps without code changes.
- Penetration Testing – Licensed human security experts simulate cyber attacks to evaluate application resilience, leveraging techniques like social engineering, password cracking, and system exploitation to uncover weaknesses.
BEST APPLICATION SECURITY PRACTICES
In most cases, Application vulnerabilities start with a compromised architecture along with design flaws which means that the application security is present in the development process—i.e., code. A security-by-design approach means that applications start off in a well-protected manner however beyond this, there are several other application security practices which are best for businesses.
Implement Robust Authentication Mechanisms
A strong authentication system is the first defense for any web application. Unauthorized access to your application can be caused by poor or incorrect authentication. Implementing a multifactor authentication is a good technique to improve your security. MFA’s requirement that users supply two or more verification factors to access an account makes it hard for attackers to break the password. In addition, the password policy needs to be strict. Support or require the use of complex, special passwords, and periodic password change. Physical attacks may also be deterred by an account blocking policy that blocks accounts after a certain number of failed login attempts. These practices may seem simple, but they are often overlooked and used as the starting point for secure user authentication.
Secure Your Data with Encryption
Another way to protect confidential information is by encrypting it. Encryption will convert readable data to a coded form, which can’t be deciphered by anyone who doesn’t have the necessary decryption key. This means that even if the data is intercepted or stolen, it’s useless to the hacker. All sensitive data, including user login credentials, personal customer information and transaction data, should be covered by encryption.
Keep Your Software Updated and Patched
To maintain web application security, it is essential to ensure that your software is up to date. Software updates deliver new features and patch vulnerabilities that hackers could exploit. Recent report found that 60 % of the breaches were caused by vulnerabilities for which a patch was available, but not applied. Attention should also be paid to the underlying platforms and library systems. The security risks can be exposed to your web application by the use of outdated components from external suppliers. The potential for exploitation is reduced by the implementation of a regular update and patches management process.
Implement A Web Application Firewall
Another layer of security to protect your web application against common exploits and vulnerabilities is a Web Application Firewall, known as WAF. Web Application Firewalls are designed to filter, monitor and block malicious web traffic that travels through an application on the Internet. It’s helping to defend against the OWASP top security threats, such as SQL injection, cross scripting site XSS and more. WAFs offer a level of security customization that is difficult to achieve with a traditional firewall. It’s a proactive approach, ready to act before the threat reaches the application.
Run Frequent Security Audits and Penetration Tests
Regular security audits and penetration tests can be used to verify the effectiveness of your safety measures. Compliance with security policies such as user access controls and configurations is checked in a security audit of your web application. Alternatively, potential security vulnerabilities are identified on the spot by penetration tests. In addition, early detection and correction of vulnerabilities can be promoted by integrating automated security testing into your DevOps cycle, which is a practice known as DevSecOps. Your web application can be strengthened against cyber threats by this combination of strict security measures and consistent testing.
GUIDE TO APPLICATION SECURITY TOOLS AND SOLUTIONS

Web Application Firewall (WAF)
A Web Application Firewall, or WAF, is a specialized security tool designed specifically to protect web applications and APIs. Installed in front of a web app or API endpoint, WAFs apply defined rulesets to monitor, filter and block potentially malicious traffic headed for the application. They operate as reverse proxies – all inbound requests to an application will first pass through the WAF for inspection before being allowed through. This allows WAFs to provide robust protection against common web app attacks like injection attacks, cross-site scripting attempts, protocol violations, bot attacks and more.
Software Bill of Materials (SBOM)
An SBOM provides a complete, formally structured list of all components, libraries, modules, packages, tools, and platforms relied upon to build and run a piece of software. SBOMs enhance security and speed up vulnerability response times by giving organizations full visibility into all incorporated software components, including nested third-party elements that may contain risks and typically go unnoticed.
Software Composition Analysis (SCA)
Software Composition Analysis (SCA) refers to a class of tools that provide visibility into all open-source libraries and components used within an application’s software supply chain. It allows risk analysis of identified components like security flaws, licenses issues, reports on outdated components needing updates/patches and alerts when new vulnerabilities emerge in existing open source dependencies.
Static Application Security Testing (SAST)
Static Application Security Testing (SAST) refers to a set of methodologies and tools used to analyze application source code, binaries, and configurations in a non-running state for coding flaws and configuration issues that are security vulnerabilities. SAST solutions scan codebases to identify vulnerable components without actually executing programs. Specific vulnerabilities detected include injection flaws, buffer overflows, improper error handling, access control weaknesses, cross-site scripting bugs and more based on rules mapping patterns in code against known issues.
Dynamic Application Security Testing (DAST)
Dynamic Application Security Testing (DAST) refers to a group of software testing methods used to detect conditions indicative of a security vulnerability in an application or software system while it is running. These tools analyse applications from the outside, testing interfaces and interactions the way a user or attacking program would by actually logging into applications and manipulating data inputs, cookies, connections and application components like databases and APIs. DAST analyses the entire application stack at once—including frontend code, backend processes, redirects, data layers and communication channels.
Interactive Application Security Testing (IAST)
Interactive Application Security Testing (IAST) is a software testing methodology that analyses applications from within to detect and report on security vulnerabilities. IAST solutions instrument application code and combine static and dynamic analysis capabilities to observe software behaviour and data flows during controlled execution. Testing is interactive in that IAST tools actively inject attacks into applications while running and monitor system response to pinpoint risks.
Mobile Application Security Testing (MAST)
Mobile Application Security Testing (MAST) refers to methodologies and tools focused on analyzing and assessing the security of mobile applications. As mobile apps become ubiquitous for entities reaching customers and enabling workforce access, specialized MAST solutions are critical for identifying vulnerabilities unique to mobile platforms and development before apps are released.
Cloud Native Application Protection Platform (CNAPP)
CNAPP refers to a consolidated security solution designed specifically to protect applications deployed in cloud environments. As more applications utilize cloud and Kubernetes-based microservices architectures, CNAPPs provide integrated runtime security across cloud-hosted components. It allows securing serverless functions and APIs from abuse, detects misconfigurations across cloud resources, blocks attack targeting Infrastructure-as-Code scripts and allows security posture management and cloud configuration benchmarks.
FINAL THOUGHTS
If one doesn’t have the right application security tools in place, it could result into serious problems as well as putting the customers and their data at risk. Cyber criminals exploit vulnerability quickly, which leaves applications unprotected against potential attacks. A single breach can irreparably harm a company’s reputation, resulting in loss of customers, income, and trust. An IBM study found that the cost of data breaches in 2023 will be $4.45 million, an increase of 15% from three years ago. In order to strengthen your brand reputation, increase customer loyalty and ultimately stimulate growth of the business, it is important to demonstrate a strong commitment to safety. Protecting information is not just about avoiding financial losses—it’s about upholding a company’s integrity and fostering a secure digital environment where customers feel safe to interact and transact.
About Author

Pankaj is a Software Applications Expert with more than 25 years’ of experience in IT Industry. Pankaj has created over 100 applications and has led the practice of the application in Wipro. Pankaj has extensive experience in Application development, application management and application modernization. He has an in-depth experience in low-code / no-code platforms as well.